From the smart home, to healthcare, to connected cars, the Internet of Things (IoT) is bringing increased connectivity to consumers and enhancing their lives in the process. However, reward does not come without risk.
The problem is that the attack surface in this ecosystem is enormous and the increased connectivity and complexity is resulting in new risks and threats to personal safety, security and privacy.
Take the threat of ransomware as an example. While the threat to PCs has been demonstrated spectacularly in recent months, an equally alarming prospect is on the horizon when it comes to ransomware, the threat to IoT and connected cars.
As the threat evolves, vulnerabilities are already present and we are likely to see attack targets spread into this area soon. Hackers continuously evolve their strategies and, as important as it is, it’s difficult for security teams to get ahead of them.
The issue is that hackers are not starting from nothing here when it comes to new attack domains. As sectors, IoT and connected cars are in their relative infancy, but hackers that are looking to perpetrate attacks in this space are bringing skills from other industries. Security teams looking to protect companies here must do the same and learn from the successes and mistakes made by other industries.
Understanding the Hacker Business Model
For companies involved in IoT devices and connected cars, it’s not a case of making yourself hack-proof, as this is pretty much impossible. Despite secure coding practices, there will always be vulnerabilities, and hackers will always find targets to attack as a result. What companies should be striving for is to make themselves, their systems and products an unviable target. They can do this by making sure they’re more secure than the other potential targets around them.
Hackers have their own business model and like most business models, it’s about ROI. This means they will almost always target the least secure element first as this requires the lowest investment in terms of both time and money to generate a potential return. The aim for IoT and automotive manufacturers should be to reduce the potential hacker ROI down so much so that they are driven to other targets.
This challenge is compounded by the fact that cyber-attack techniques and strategies are constantly evolving. To use an automotive safety analogy, this means that cybersecurity is not a cement wall that you can crash a vehicle into ten times and get the same result.
In cybersecurity, the wall will be different every time and therefore the outcome will be different each time. To prepare for this new environment, the IoT and automotive industries need to think deeper about security and re-think strategies.
The Dangers of Connected Cars
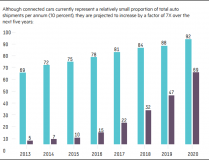
In recent years, the rapid innovation in IoT and autonomous technology has been impressive. Unfortunately, eagerness for autonomous technology has resulted in security becoming an afterthought in many cases and therefore, there are many vulnerabilities in today’s connected cars.
Hackers continuously evolve their attack strategies and have exploited vulnerabilities to access vehicle electronic control units (ECUs), controller area network (CAN) bus systems, intelligent transportation systems (ITS) or even automotive apps through the cloud.
The UK government recently issued stricter security guidelines for the security of connected cars. A step in the right direction, these guidelines mirror those set by the National Highway Traffic Safety Administration in the US and look to be based on industry best practices outlined in the J3061 Standard (Cybersecurity Guidebook for Cyber-Physical Vehicle Systems) from SAE International. These guidelines brought together security best practices from other industries as a starting point and are evolving with the growing security knowledge in the automotive industry.
To address the vulnerabilities, a well-defined strategy is required where OEMs, tier-one suppliers and IT service providers work together to not only define cybersecurity solutions, but more importantly, understand vulnerabilities from a hacker’s perspective. However, while understanding both threats and risks is a good starting point, to be successful in the long term, new practices will have to be adopted.
Securing the Environment
The clear starting point for IoT and automotive manufacturers is to conduct a threat assessment on products – this will help establish where they are in the ecosystem in terms of security, what the weaknesses and risks are and the action that needs taking. This will be an educational process as these factors will likely vary from product to product.
Organizations must then adopt a defence in-depth approach to cybersecurity. This approach involves many layers of security being implemented throughout the network, rather than simply protecting systems from the outside-in (perimeter security).
A security in-depth strategy for the endpoints incorporates run-time integrity verification; this is crucial in mitigating threats like ransomware in automotive, as with this strategy, even if the hacker finds a way to penetrate the perimeter, they won’t be able to hold the car hostage.
IoT and automotive companies are realizing the importance of a robust security strategy and many are starting down the right path. The important thing now is to learn from the security knowledge in other industries and find a way to match the evolutionary pace of the hacking groups that threaten their products and revenues.
Author – Daniel Thunberg
Courtesy of info security